So it's finally July, time to pack for DEFCON, follow
@defconparties on Twitter and decide which
villages to visit and which
talks to attend.
There's a new hacking competition this year called
SOHOpelesslyBroken, presented by ISE and EFF. The objective on
Track 0 is to demonstrate previously unidentified vulnerabilities in off-the-shelf consumer wireless routers.
Track 1 will hold a live CTF for the duration of DEFCON. CTFs are always fun and this contest involves hacking real embedded devices, what makes it even more fun.
 |
| Yes, that's my workstation =P |
I'm particularly interested on the
EFF Open Wireless Router, but they didn't disclose details about the device yet. According to the
event rules, the
ASUS RT-AC66U (HW Ver. A2) [Version 3.0.0.4.266] is one of the possible targets. As I had a spare RT-AC66U at home, I decided to write a quick guide for everyone interested in participating in this
competition CTF.
recon
The first thing to do is to find the firmware and its source code. Hopefully, Asus RT-AC66U is GPL'ed and we can easily find its source online. The version used for the contest is an old one, from 2012. In order to perform a better analysis, we are going to grab the sources and the firmware from v3.0.0.4.266 and v3.0.0.4.376.1123 (the most recent one as of this writing).
Many firmware versions were published between these two releases, we can review the changelogs to find security issues:
According to the rules, we have to identify and exploit a 0-day vulnerability. We can combine different flaws with known issues in order to score points. If the vendor had silently patched an issue and you create an exploit for it, that should be scored as a valid 0-day (I'm not going to start discussing terminologies here).
Now that we have the source code, it's time to extract and audit it: The
CTF Field Guide from Trail of Bits has some good resources on
Auditing Source Code. You can use tools like
Beyond Compare,
Araxis Merge and
WinMerge on Windows platforms or
Meld if you're more of a Linux user.
Let's focus on the "/asuswrt/release/src/router/" directory, comparing these two folders using Meld:
There are many security advisories for this router: if you want to find 0-days you should look for disclosed vulnerabilities and exploits to avoid duplicates (believe me, this is the hardest part). Some references:
Points are deducted from your score if your exploits requires special system configurations and specific information. If you want to score lots of points, you should be targeting default services and processes.
The USB application tab on the RT-AC66U allows the user to set up a series of services like FTP, DLNA, NFS and Samba:
MiniDLNA is also a nice a target. It should be pretty easy to find vulns for the service using
Zachary Cutlip's
research, as he broke it multiple times.

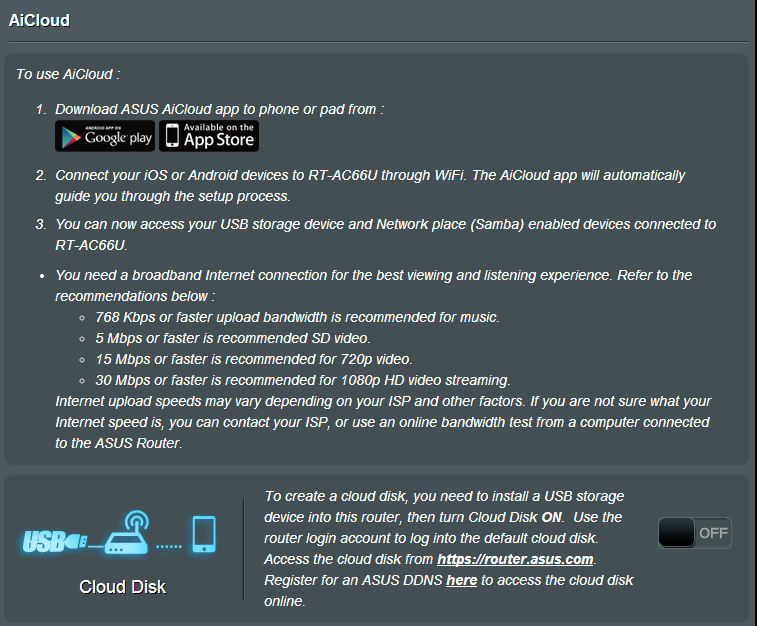
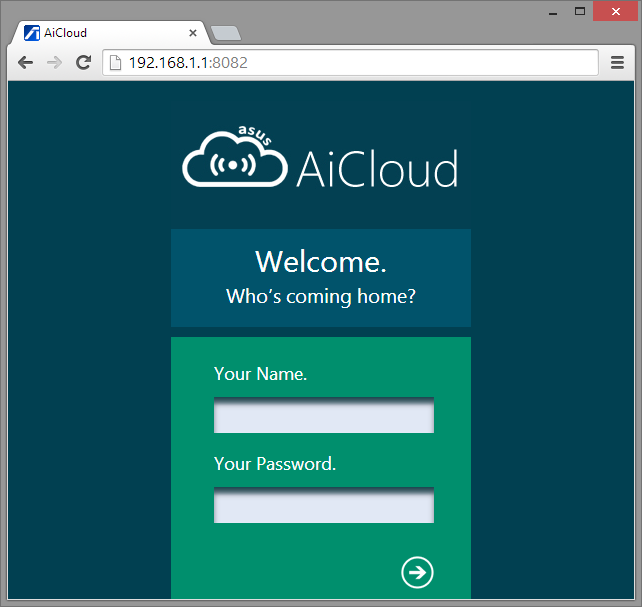
Another
potentially vulnerable service is AiCloud: it links your home network to an online Web storage service and lets you access it through a mobile application:
forensic
While part of the team audits the source code, the forensics guys should be unpacking the firmware using binwalk + fmk:
You may remember
binwally, the tool I developed to
perform binary tree diff using fuzzy hashing. Binwalk has its own option to
perform fuzzy hashing against files and directories:
Most vendors (like Asus) won't open source their entire code base. You may need to reverse proprietary drivers and binary blobs in order to find some good vulns. ACSD is a particularly interesting binary because it was removed from newer firmwares (v3.0.0.4.374.130+) due to a
vuln disclosed by
Jacob Holcomb:
The binaries are MIPS and Little Edian:
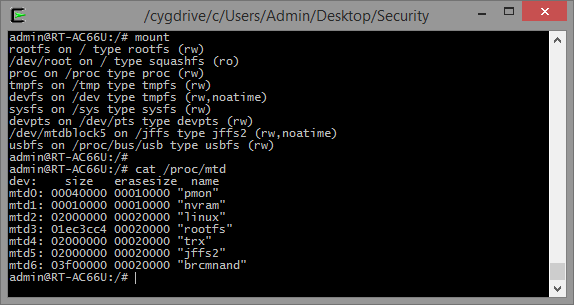
It's also important to learn more about the filesystem. The OpenWRT Wiki has a nice
article on Flash Layouts. The
MTD subsystem for Linux provides access to flash devices, creating fully functional filesystems. SSH to the device and map the mount points and partitions:
The NVRAM partition is very valuable for us because it stores all the configuration parameters. We can view its content by dumping the corresponding partition (mtd1) or by issuing the "
nvram show" command:
Another interesting partition is the bootloader (pmon). It has some LZMA compressed data and the boot process provides a failsafe mechanism to recover from a bad flash.
reverse
Time to start the reversing tasks. We need some basic tools like gdb, gdbserver and strace to start debugging the binaries: we could either cross compile them or set up
Optware/Entware to install prebuilt packages.

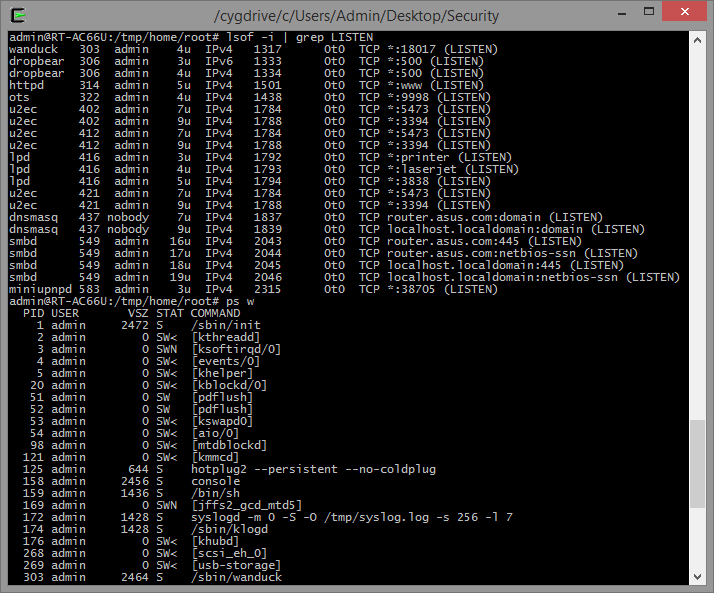
Wanduck (GPL_RT_AC66U_VER3004266/asuswrt/release/src/router/rc/wanduck.c) is an interesting process to analyze. It starts by default and binds a pseudo HTTP server on port 18017. The HTTP server redirects every request to the main administrative interface and, for some reason, it drops requests to URL's ending with ".ico".
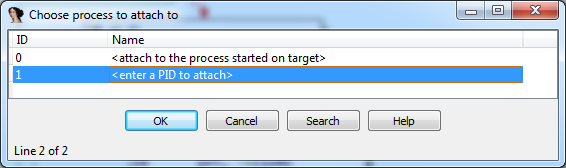
Let's find out why: start gdbserver on the remote target (gdbserver --multi localhost:12345 &) and connect to your debugger of choice. If you're using Ida Pro, open the binary "/sbin/wanduck" and set the processor type to "mipsrl".
Navigate to the
handle_http_req function and set a breakpoint on the
dst_url comparison:
Enter the gdbserver's host and port under "Debugger / Process Options" and attach to the corresponding PID.
Resume the process (F9) and make an HTTP request to http://192.168.1.1/x.ico. The debugger will stop at the defined breakpoint and you can now inspect the registers and the memory.
If you want to find reverse engineering targets, search for folders named "
prebuilt" under "GPL_RT_AC66U_VER3004266/asuswrt/release/src/router/". Some interesting binaries:
- /acsd/prebuilt/acsd
- /webdav_client/prebuilt/webdav_client
- /asuswebstorage/prebuilt/asuswebstorage
- /eapd/linux/prebuilt/eapd
- /nas/nas/prebuilt/nas
- /flash/prebuilt/flash
- /et/prebuilt/et
- /wps/prebuilt/wps_monitor
- /ated/prebuilt/ated
- /wlconf/prebuilt/wlconf
The mobile AiCloud app might reveal some interesting information about how the device works. If you reverse the APK or use an intercepting proxy you can identify the app's initial HTTP request:

You see that strange ddns_hostname? That's a crypto task =)
crypto
The POST request tries to register a new Dynamic DNS using the asuscomm.com service. If we search for the term
asuscomm.com on the RT-AC66U source code, we can easily find the function that generates this DDNS:
According to
WikiDevi, the following OUIs are currently being used by the RT-AC66U:
- 08:60:6E (1 E, 1 W, 2011)
- 10:BF:48 (1 E, 2 W, 2011)
- 30:85:A9 (3 E, 3 W, 2011)
- 50:46:5D (1 E, 2 W, 2012)
Using this information we can map the IP address for every single router using AiCloud. Let's generate a list of all the possible MAC addresses and brute force the hostnames using
this cool trick from
mubix.
If you're too lazy to run these commands, you can simply search for
asuscomm.com on
Shodan:
AiCloud runs on ports 8082 and 443 by default. The fact that anyone can easily map the routers running this service could be very worrisome,
right?
Another interesting crypto exercise is to reverse the algorithm used to generate the WPS device PIN. You can view the currently PIN and secret_code by issuing the following command:
nvram show | grep -E "secret_code|wps_device_pin". Search for these variables in the source code and use this information to create you own WPS Keygen (don't forget to include a chiptune from
pouet.net).
You can also test the entropy from the crypto keys generated by the device. Check the slides from the "
Fast Internet-wide Scanning and its Security Applications" to gather some ideas:
web
There are so many things to test on the Web application that I'll focus on a few different approaches. The router's administrative interface has no CSRF protection. It has the traditional ping command injection and lots of XSS vectors.
The HTTP daemon is based on microhttpd. It has some basic Directory Traversal Protection on httpd.c:
We can shamelessly steal
hackerfantastic's
idea and test for potential bypasses (there's an extensive
list of LFI tests at
Seclists):
The web server has some mime handler exceptions that were "supposed to be removed":
get_webdavInfo.asp is accessible without authentication and displays lots of sensitive information from the device and the network:
We can modify the nvram variables used to display this page and backdoor the router with a XSS payload, for example.
Some sensitive operations use the
nvram_get and
nvram_safe_get function. Some settings are stored using the
nvram_set function. If the router does not sanitize the data being stored and retrieved from the NVRAM you may perform some kind of NVRAM Injection (remember, 00, %0A, %0D and `reboot` are always there for you).
AiCloud is a *very* vulnerable service that can be
easily exploited too. When you activate the service, the router starts a lighttpd daemon on port 8082 (or 443 on newer firmwares) and offers the option to share your files online. The only caveat is that the username and password screen can be bypassed by visiting the /smb/ URL (read the source, Luke):
I wrote a simple AiCloud crawler that exploits this bug on RT-AC66U v3.0.0.4.266. It lists all the files/paths from the router (including the attached USB devices).
Last, but not least, don't forget to compare the differences between the files in the
www directory. This path stores all the web components and scripts used by the web application.
bonus
Why not trying to open the hardware case without voiding the warranty seal? You may need some tips from the guys at the
DEFCON Tamber Evident Village.
misc (a.k.a. Conclusion)
Hacking the Asus RT-AC66U is a very good exercise for the newcomers on router hacking. Most of its source code is available online and we can easily find lots of exploits and advisories for it. You may not have noticed but we tested every single aspect of the
OWASP Internet of Things Top 10. Recent rumors indicate that this router is going to be used as the base for the OWASP IoT Webgoat and the Damn Vulnerable Embedded Linux.
Some additional approaches you should be taking and that should be awarded extra points during the contest:
- Rewrite the bootloader to create a backdoored dual-boot partition
- Backdoor the device in a way that firmware upgrades won't affect it
- Brick the device remotely
- Reprogram the LED to create a PONG game
There are many things that I still want to write about, but I'm saving that for future posts. If you are going to participate in the
SOHOpelesslyBroken CTF and find this guide useful, feel free to ping me and let's get a coffee together during DEFCON/BsidesLV/Blackhat =)